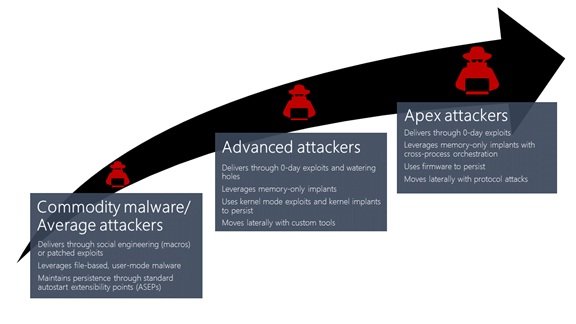
Microsoft says that it would showcase its investments made to enhance instrumentation and detection of in-memory techniques in a three-part series. The series would cover- In the first post, their main focus was on cross-process injection. They have illustrated how the enhancements that will be available in the Creators Update for Windows Defender ATP would detect a broad set of attack activities. This would include everything starting from commodity malware which has attempted to hide from plain view to the sophisticated activity groups which engage in targeted attacks.
How Cross-process Injection helps attackers
Attackers are still managing to develop or purchase zero-day exploits. They are putting more emphasis on evading detection to protect their investments. To do this, they rely mostly on in-memory attacks and kernel privilege escalation. This allows them to avoid touching the disk and remain extremely stealthy. With cross-process injection attackers get more visibility into the normal processes. Cross-process injection conceals malicious code inside benign processes and this makes them stealthy. According to the post, Cross-process injection is a two-fold process:
How Windows Defender ATP detects cross-process injection
The blog post says that the Creators Update for Windows Defender ATP is well equipped to detect a broad range of malicious injections. It has instrumented function calls and built statistical models for addressing the same. The Windows Defender ATP Research Team tested the enhancements against real-world cases to determine how the enhancements would effectually expose hostile activities that power cross-process injection. The real-world cases quoted in the post are Commodity malware for cryptocurrency mining, Fynloski RAT and Targeted attack by GOLD. Cross-process injection, like other in-memory techniques, can also evade antimalware and other security solutions which focus on inspecting files on disk. With Windows 10 Creators Update, Windows Defender ATP will be powered to provide SecOps personnel with additional capabilities to discover malicious activities leveraging cross-process injection. Detailed event timelines, as well as other contextual information, is also provided by Windows Defender ATP which can be useful to the SecOps personnel. They can easily use this information to quickly understand the nature of attacks and take immediate response actions. It is built into the core of Windows 11/10 Enterprise.